密码认证方式(认证加密方式)
简介
对于安全认证来说,也是无线比较重要的一块,在SOHO级别以及小型环境中,比较倾向于预共享的方式进行认证,也就是配置一个大家知道的密码,输入后就能连接到无线网络,常用的有WEP、WPA、WPA2,WEP已经渐渐的淘汰了,非常容易被破解,推荐的是WPA2的AES,对应小型环境或者SOHO级别的来说还是比较容易部署的。当然认证还有很多,比如基于MAC地址认证、dot1x方式 或者portal网页认证等,这些方式会在后续陆续演示。
掌握目标
1、AC的基本业务配置
2、认证方式的配置

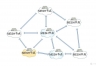
拓扑写了对应的IP网段,以及各自的VLAN信息,可以对应配置看
路由的配置
interface GigabitEthernet0/0/0
ip address 10.1.200.1 255.255.255.0
#
interface LoopBack100
ip address 100.100.100.100 255.255.255.255
#
ospf 1 router-id 1.1.1.1
default-route-advertise always
area 0.0.0.0
network 10.1.200.1 0.0.0.0
AC的配置
#
interface Vlanif100
ip address 10.1.100.1 255.255.255.0
dhcp select interface
#
interface Vlanif101
ip address 10.1.101.1 255.255.255.0
dhcp select interface
dhcp server dns-list 8.8.8.8
#
interface Vlanif102
ip address 10.1.102.1 255.255.255.0
dhcp select interface
dhcp server dns-list 8.8.8.8
#
interface Vlanif103
ip address 192.168.103.1 255.255.255.0
dhcp select interface
dhcp server dns-list 8.8.8.8
#
interface Vlanif200
ip address 10.1.200.2 255.255.255.0
说明:该VLAN接口地址一个是用于与AR路由器相连,其余的是作为无线客户端的网关
interface GigabitEthernet0/0/1
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 102
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 to 102
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 200
说明:这里由于AP是双频的,也可以每个AP发送多个SSID,所以要允许对应的VLAN流量。
interface Wlan-Ess0
port hybrid untagged vlan 101
#
interface Wlan-Ess1
port hybrid untagged vlan 102
#
interface Wlan-Ess2
port hybrid untagged vlan 103
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 10.1.200.2 0.0.0.0
area 0.0.0.1
network 10.1.100.1 0.0.0.0
network 10.1.101.1 0.0.0.0
network 10.1.102.1 0.0.0.0
network 192.168.103.1 0.0.0.0
wlan
wlan ac source interface vlanif100
ap id 0 type-id 19 mac 00e0-fc03-7820 sn 210235448310F3277942
ap id 1 type-id 19 mac 00e0-fc03-9730 sn 2102354483100A13F850
wmm-profile name wmm1 id 0
traffic-profile name tra1 id 0
security-profile name open id 0
security-profile name wep40 id 1
wep authentication-method share-key
wep key wep-40 pass-phrase 0 simple 12345
security-profile name wpapsk id 2
security-policy wpa
wpa authentication-method psk pass-phrase simple huaweipsk encryption-method ccmp
定义了3种不同的认证方式,分别为open、WEP与WPA
service-set name vlan101 id 0
wlan-ess 0
ssid vlan101
traffic-profile id 0
security-profile id 1
service-vlan 101
service-set name vlan102 id 1
wlan-ess 1
ssid vlan102
traffic-profile id 0
security-profile id 2
service-vlan 102
service-set name guest103 id 2
wlan-ess 2
ssid guest103
user-isolate
traffic-profile id 0
security-profile id 0
service-vlan 103
radio-profile name 2g id 0
wmm-profile id 0
ap 0 radio 0
radio-profile id 0
service-set id 0 wlan 1
service-set id 1 wlan 2
service-set id 2 wlan 3
ap 1 radio 0
radio-profile id 0
channel 20MHz 6
service-set id 0 wlan 1
service-set id 1 wlan 2
service-set id 2 wlan 3 #
最后记得comm下发业务给AP即可。

上一篇回顾
下一篇学习
由浅入深玩转华为WLAN-9 基于无线的MAC地址认证